Architecture
Arcjet has been architected around a few key principles:
- Proper security protections need the full context of the application, which is why security rules and protections should be located alongside the code they are protecting.
- Security rules should be easy to test. You should be able to run them in development as well as production.
- Arcjet should not interfere with the rest of the application. It should be easy to install, must not add significant latency to requests, and should not require changes to the application’s architecture.
Video: how Arcjet works
Section titled “Video: how Arcjet works”Primitives
Section titled “Primitives”Arcjet provides a set of key primitives which can be used to build security functionality. Each primitive can be used independently or combined as part of a pre-configured product.
Core primitives
Section titled “Core primitives”- Shield - Protect against common attacks.
- Rate limiting - Limit the number of requests from a client over a period of time.
- Bot protection - Detect and block automated clients.
- Email validation - Check that an email address is valid.
- Sensitive information - Protect against clients sending you PII that you do not wish to handle.
- Filters - Block requests using expressions over request metadata.
Components
Section titled “Components”Arcjet has two components:
- Arcjet SDK installed into your application.
- Arcjet Cloud API used to make or report decisions.
Arcjet SDK
Section titled “Arcjet SDK”The SDK integrates Arcjet into your application. Security rules are configured in your code using the SDK and they execute either through a middleware layer or directly from your application code. You can inspect the response in your code and decide how to handle it. This could be as simple as blocking the request or more advanced like flagging an account for review.
The SDK includes a WebAssembly module which is used to analyze requests locally in your own environment. Where possible, a decision is taken locally and then reported to Arcjet so that you can view the details in the Arcjet dashboard. Decisions may also be cached in memory.
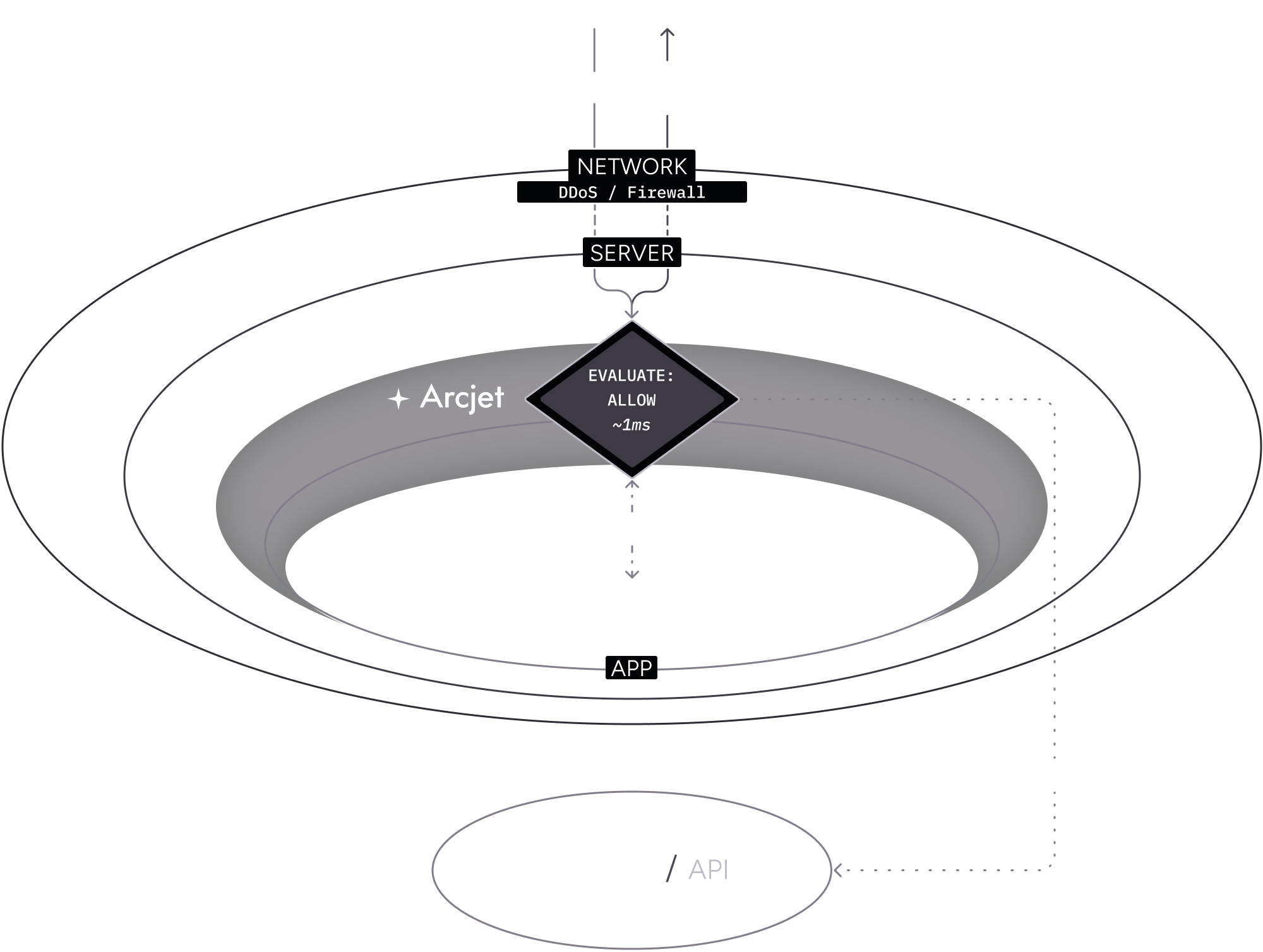
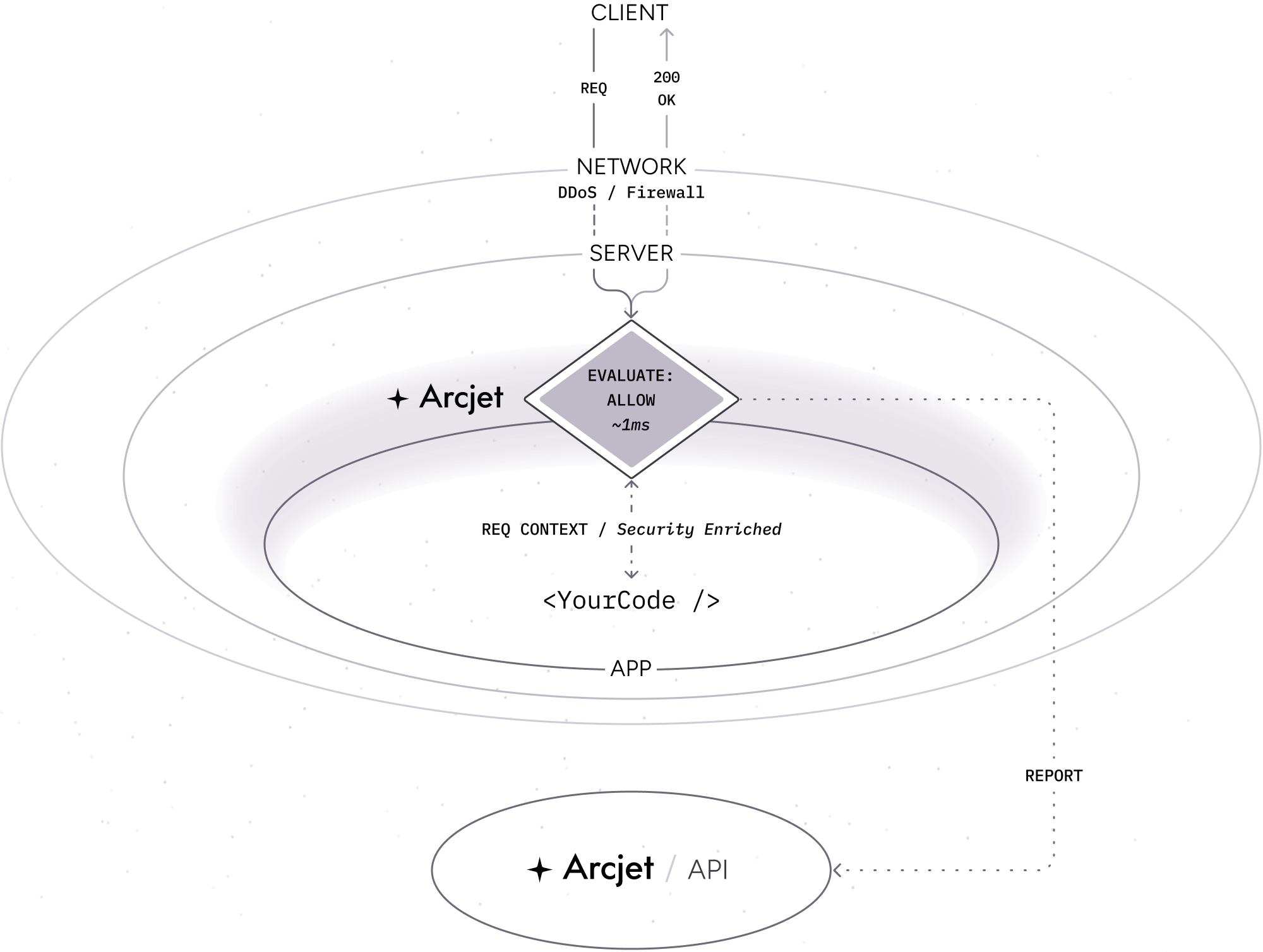
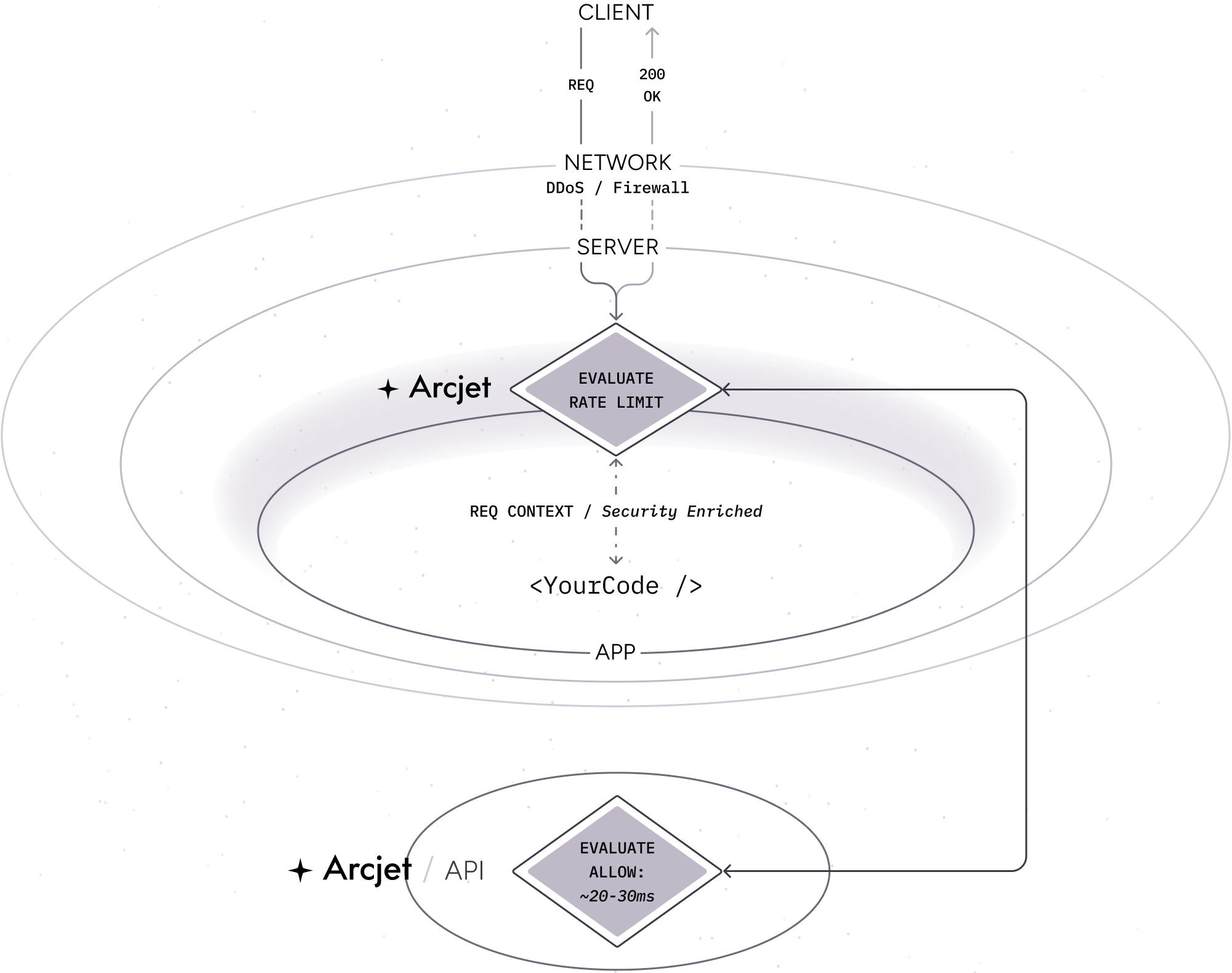
Example: Local analysis
Section titled “Example: Local analysis”In this example flow:
- A client makes an HTTP request to your application.
- Your platform applies standard DDoS protection through their network firewall. Most platforms provide DDoS protection transparently and out of the box for no extra cost.
- Your server (container, serverless function, VM, etc) receives the request.
- The Arcjet SDK is configured as middleware so it intercepts the request before it reaches your application code. Arcjet analyzes the request locally based on the rules you configured, then decides to allow the request.
- Arcjet returns the result and your application code continues to execute as normally. You can inspect the decision to understand why Arcjet came to that conclusion. An asynchronous report is made to the Cloud API for post-request analysis.
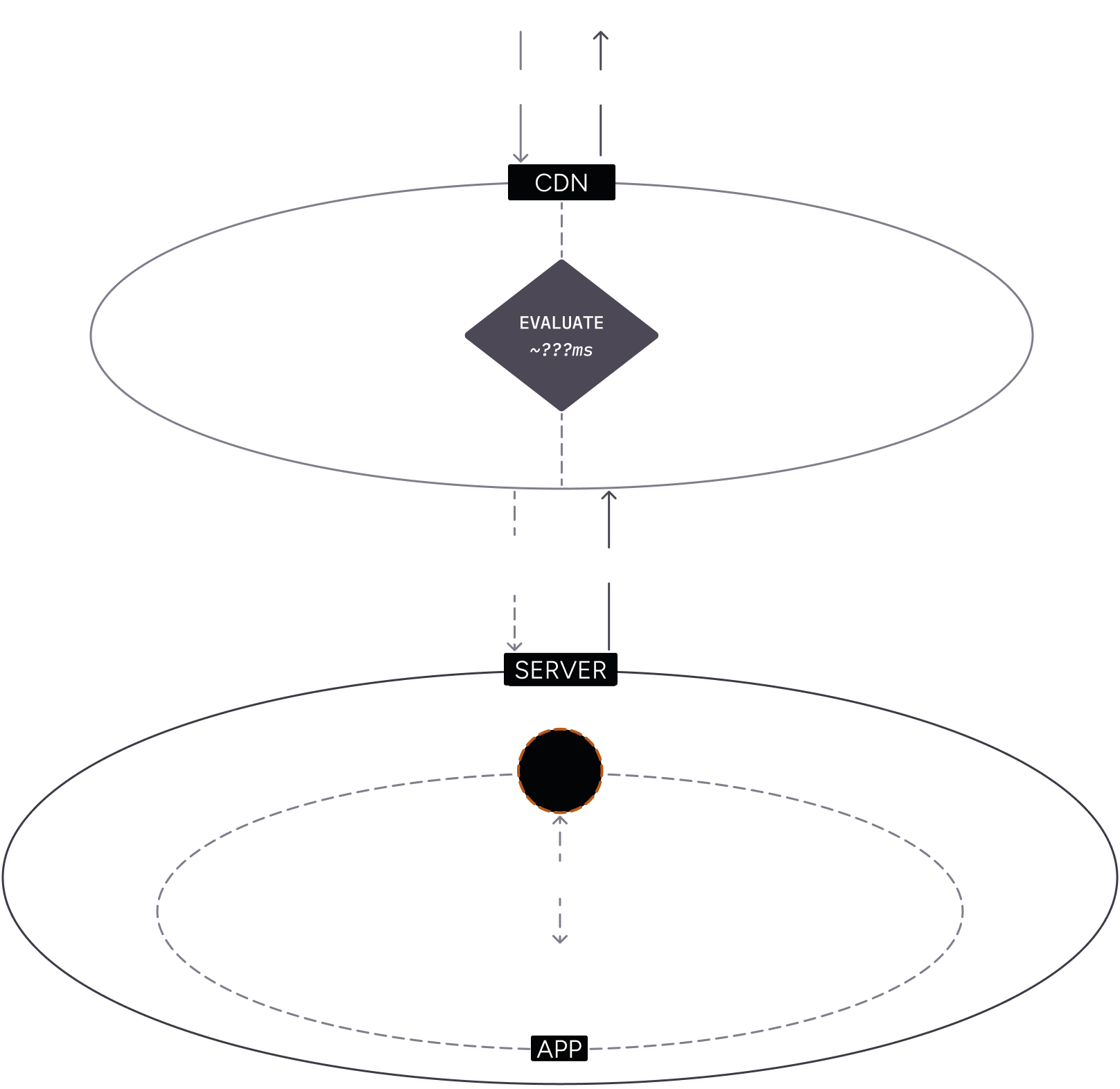
Contrast with traditional CDN security services
Section titled “Contrast with traditional CDN security services”Traditional CDN security services are typically implemented as a reverse proxy in front of your application. The security service is a separate entity from your application, rules can’t be adjusted dynamically because it does not have access to the full context of the request, and it can’t be tested locally.
This can lead to false positives and false negatives as the service does not have the full context of the application.
For example:
- A client makes an HTTP request to your application.
- The request is intercepted by the CDN security service.
- The service analyzes the request and decides to block the request.
- The request is blocked and the client receives an error message, but your application code never sees the request. This can lead to false positives where legitimate requests are blocked. If your application had seen the request, it may have been able to determine that it was legitimate e.g. because the client was logged in.
- Or, the request is allowed and your code runs, but it has no idea that the request was analyzed by the CDN security service and why the request was allowed.
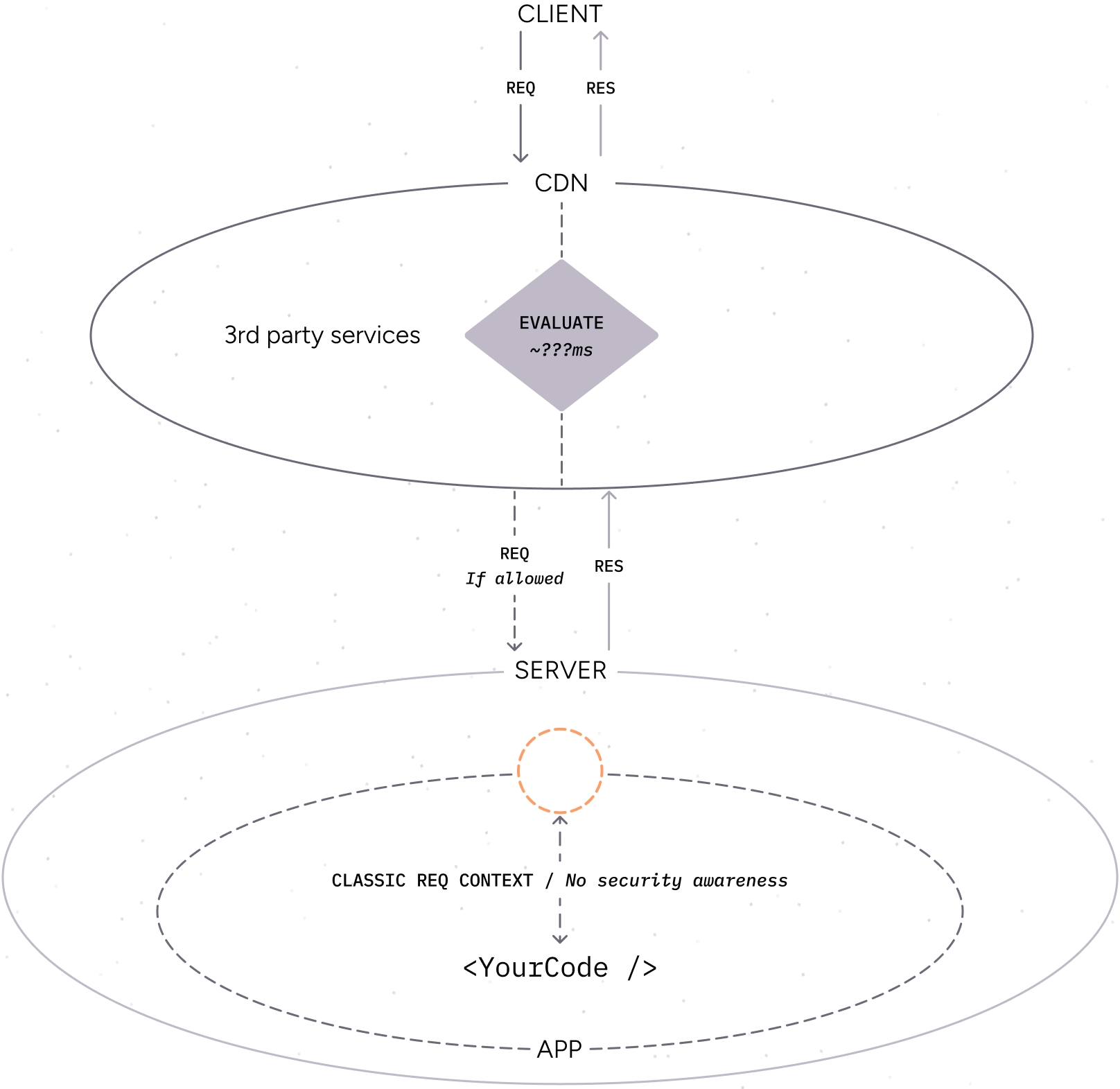
Arcjet Cloud API
Section titled “Arcjet Cloud API”In many cases, Arcjet can make a decision locally and report that decision asynchronously to the Cloud API. However, there are some cases where Arcjet must make a decision in the cloud.
For example, if you are want to enforce a rate limit, the number of requests for each client must be tracked. This means you typically need to manage something like Redis or another database, something that is particularly tricky in serverless environments. If you are using Arcjet, this is managed for you with no additional infrastructure. The Arcjet SDK will make a call to the Cloud API to get the current rate limit for the client.
The API has been designed for high performance and low latency, and combines all security functionality in one request. This means it typically outperforms other similar solutions. Arcjet will also attempt to cache decisions locally using an in-memory cache. In many cases, the total latency will be less than 1ms.
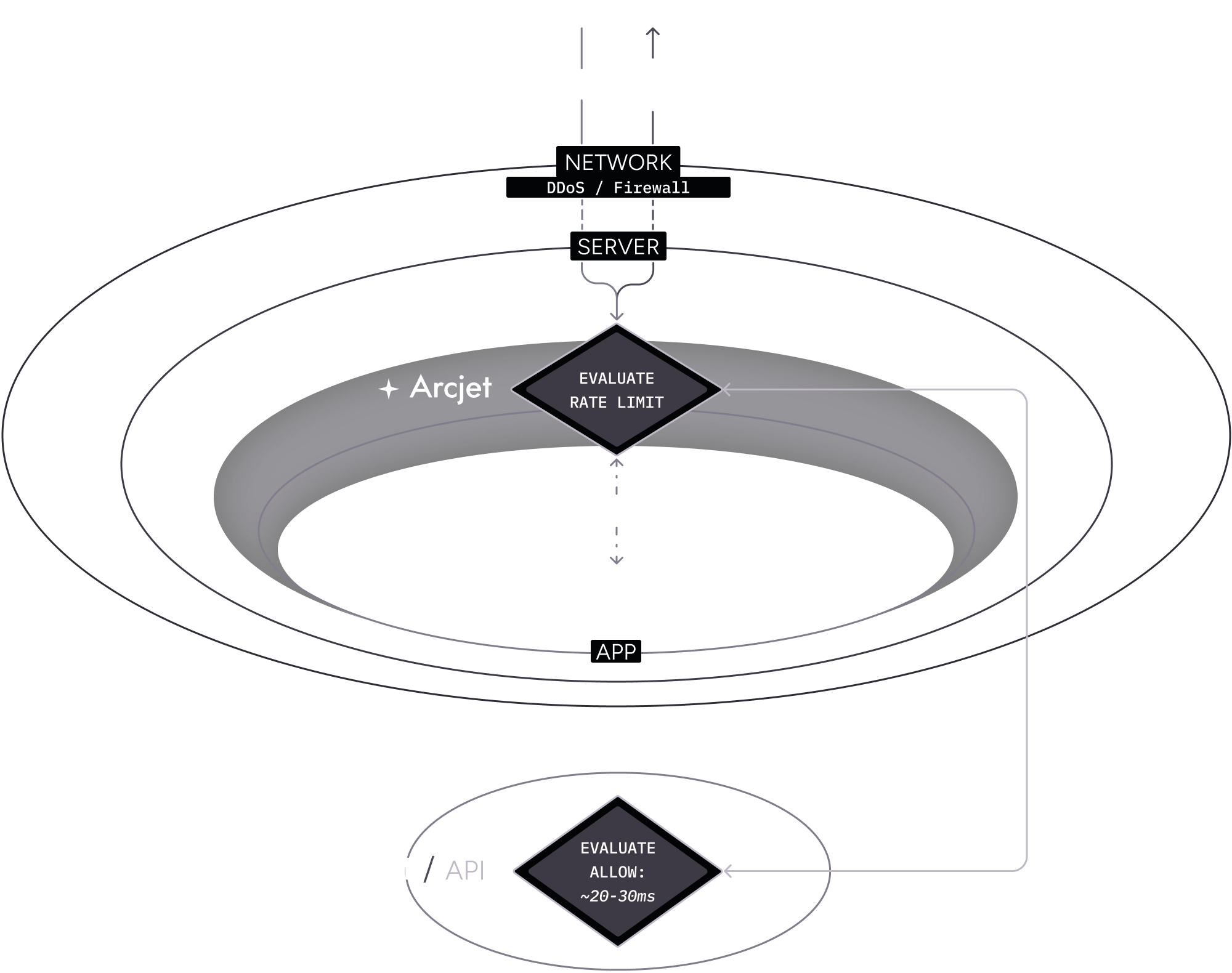
Example: Rate limit rule (allow)
Section titled “Example: Rate limit rule (allow)”- A client makes an HTTP request to your application. It passes through the network level DDoS protection as described above then reaches your server.
- The Arcjet SDK is configured with a rate limit rule on an API route. The SDK passes the request context through to the Cloud API which checks the rate limit for that client and then returns an allow decision.
- The SDK returns the details and your application code continues to execute as normal.
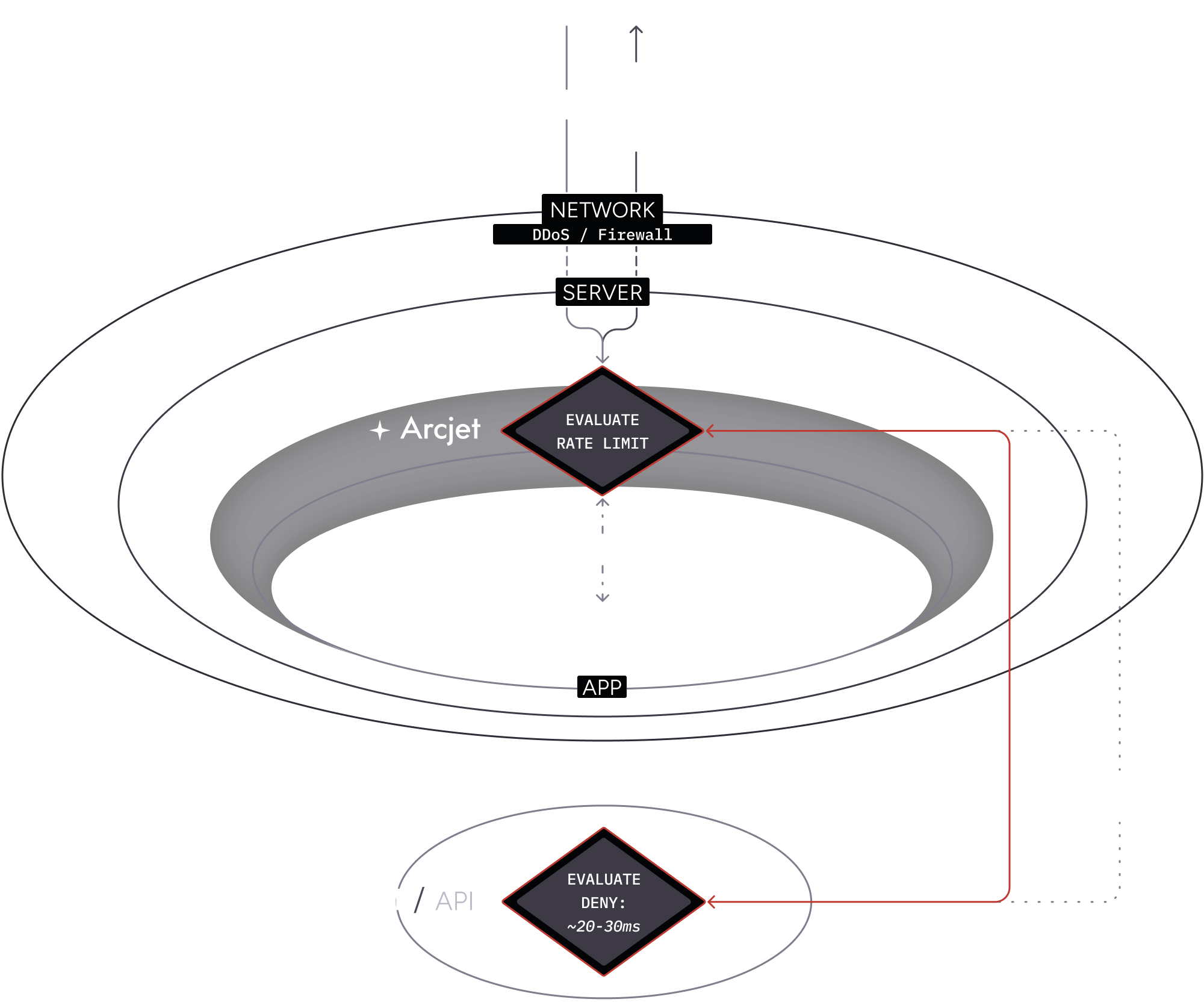
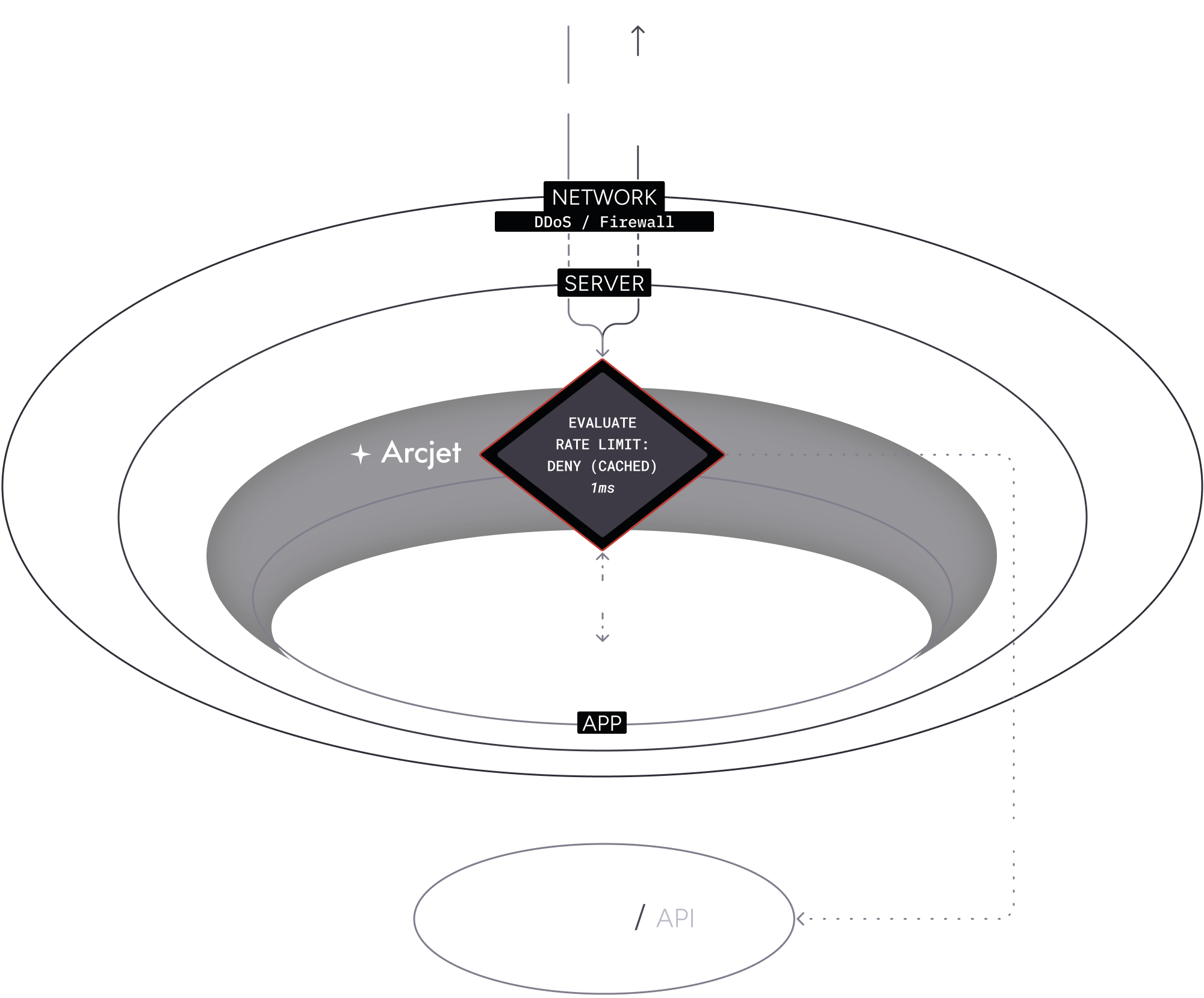
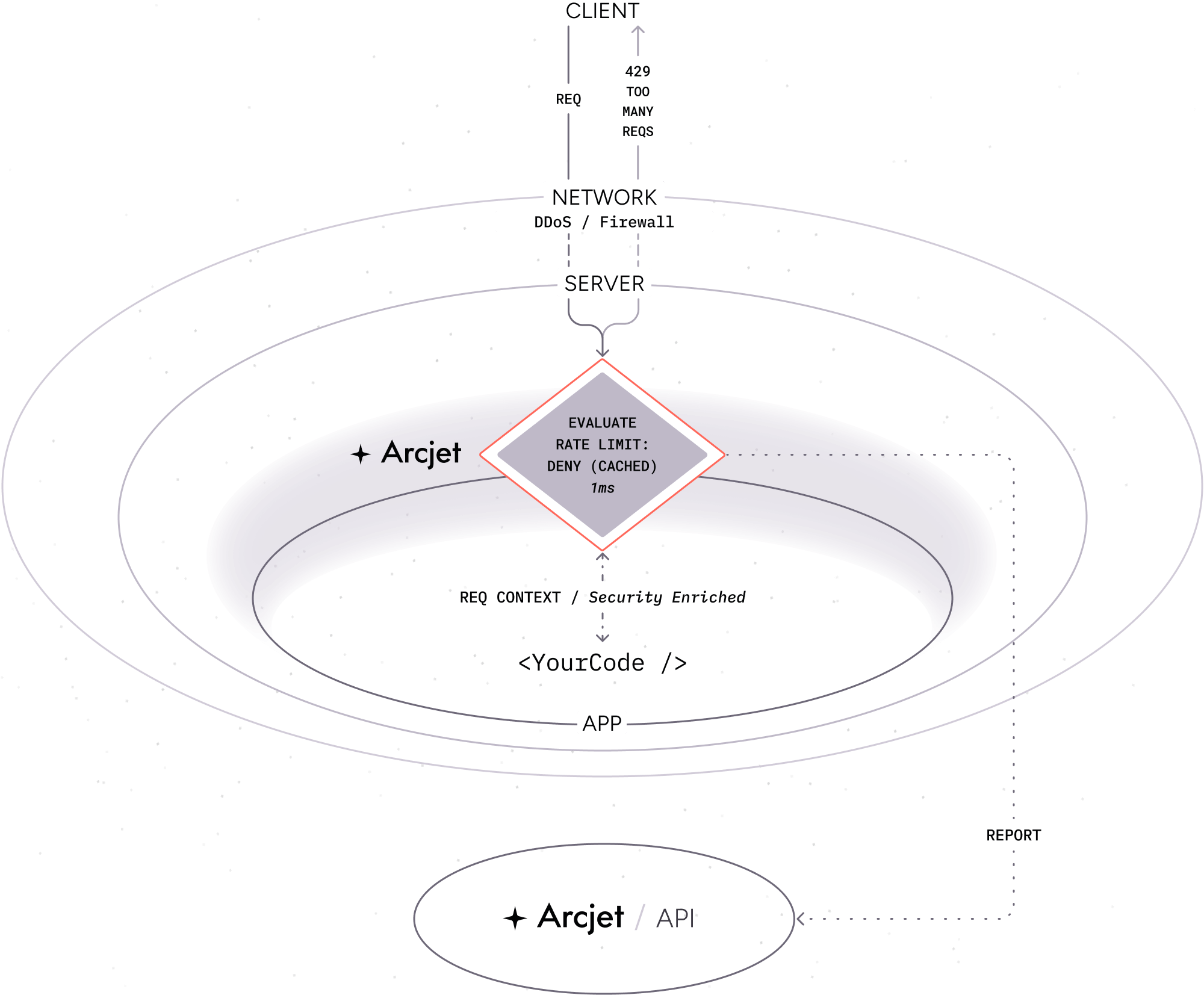
Example: Rate limit rule (deny)
Section titled “Example: Rate limit rule (deny)”This time when the request is received, the rate limit has been exceeded.
- A client makes another request to your application with a rate limit rule configured.
- As before, the SDK passes the request context through to the Cloud API which determines the limit has been exceeded.
- The SDK provides the details and your application code returns a 429 response to the client.
- The decision is also cached locally so that subsequent requests which match the rate limit rule does not need to rely on a call to the Cloud API.
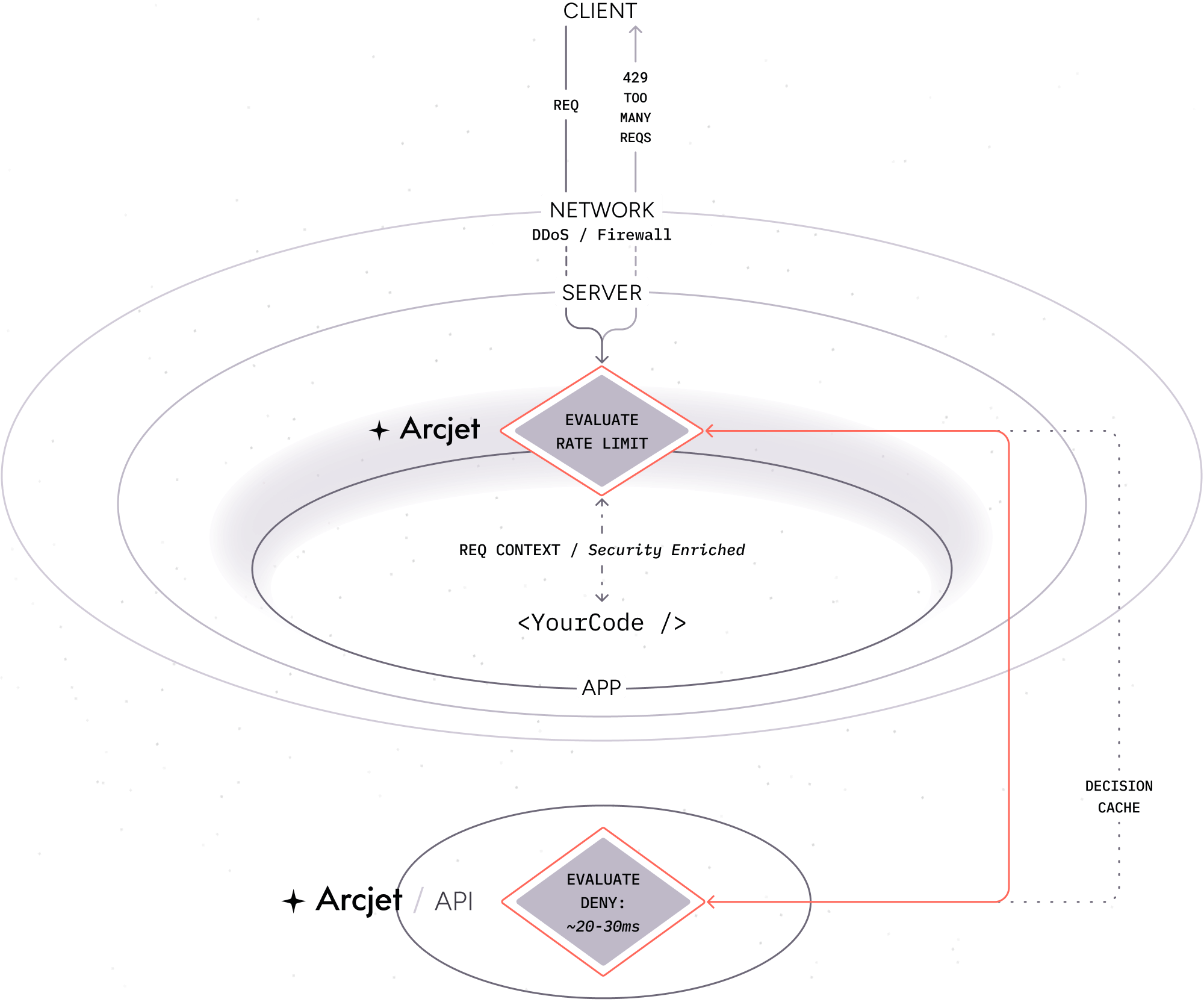
This means that if the same client makes another request, the SDK will read from the local cache and return the response immediately:
When the API is required
Section titled “When the API is required”A call to the Cloud API is required when:
- A Shield rule is configured. Behavior must be compared across multiple requests to protect against common attacks.
- A Rate limiting rule is configured. Client state must be tracked across requests to enforce the rate limit. Arcjet manages tracking this state for you so you do not need deal with other infrastructure or services.
- A Bot protection rule is configured and local analysis of the client request does not provide enough information to make a decision. Local analysis is limited to the request headers whereas the Arcjet API also checks a live database of known bots, IP addresses, VPNs, proxies, Tor nodes, and other relays.
- An Email validation rule is configured and the email address syntax is valid. The Arcjet SDK analyzes the email address locally to check the syntax. If it is invalid, the SDK will return a decision immediately. If it is valid, the SDK will make a call to the Cloud API to verify the email address e.g. does it have a valid MX record or is it a disposable email address.
- A Filter rule is configured that inspects
ip.src.*IP address fields such asip.src.vpn,ip.src.asnum.domain, orip.src.country. These fields require data from our IP reputation database so a call to the Cloud API is required. Other fields are analyzed locally.
API latency
Section titled “API latency”The Arcjet SDK tries to do as much as possible asynchronously and locally to minimize latency for each request. This adds less than 1ms of overhead to a typical request.
When a call to the Cloud API is required there is some additional latency before a decision is made. The Cloud API has been designed for high performance and low latency, and is deployed to multiple regions around the world. The SDK will automatically use the closest region which means the total overhead is typically no more than 20-30ms, often significantly less.
Arcjet only ever makes a single call to the API regardless of the number of rules configured.
Where a decision has been cached locally e.g. blocking a client, Arcjet will continue to function even if the service is unavailable. In the event of a network problem or outage and a call to the API is needed, the Arcjet SDK defaults to failing open so all requests will be allowed. This is a deliberate design decision to ensure that your application continues to function even if there is a problem, but you can configure the SDK to fail closed if you prefer. See an example of how to handle errors and fail open or closed in the Node.js SDK reference.
Timeout
Section titled “Timeout”The total overhead when connecting to the Arcjet Cloud API is typically no more than 20-30ms, often significantly less. There is a timeout in place to prevent waiting for a response indefinitely in case of problems. This value is configurable in the SDK. The default is 500ms in production and 1000ms in development.
The reason for this difference is that in production your app usually runs on a server close to the Cloud API. In development your app may run on a laptop some distance away from the Cloud API. That introduces additional latency.
To illustrate, a developer in New Zealand may have to connect to the Arcjet Cloud API running in the closest cloud region, which might be Australia. In contrast, a user would connect to your application and then the application would connect to the closest Arcjet Cloud API, usually within the same region.
A shorter timeout may result in faster failure responses but could lead to increased error rates if the Cloud API needs time to respond. Conversely, a longer timeout may improve success rates but could lead to a less responsive experience.
For more info, see the post Minimizing latency for humans & machines on the Arcjet blog.
Request analysis
Section titled “Request analysis”Arcjet analyzes every request to your application in real-time. This is based on the rules you configure and the SDK provides the result so you can decide whether to deny or allow requests, or to take other actions.
Post-request analysis is also performed by the Arcjet platform. This allows Arcjet to detect other types of attacks, such as SQL injection or other suspicious activity. This is threshold-based to avoid false positives. Once a client reaches a threshold of suspicious activity, Arcjet will issue a deny decision for that client for a period of time.
This threshold is dynamic and regularly updated based on the latest attack patterns. This protection is automatic and does not require any configuration. You can see the details of all requests, including those that are denied, in the Arcjet dashboard.
The results of this analysis are used regardless of the rules configured. This means Arcjet is continuously analyzing requests to your application and protecting it from attacks.
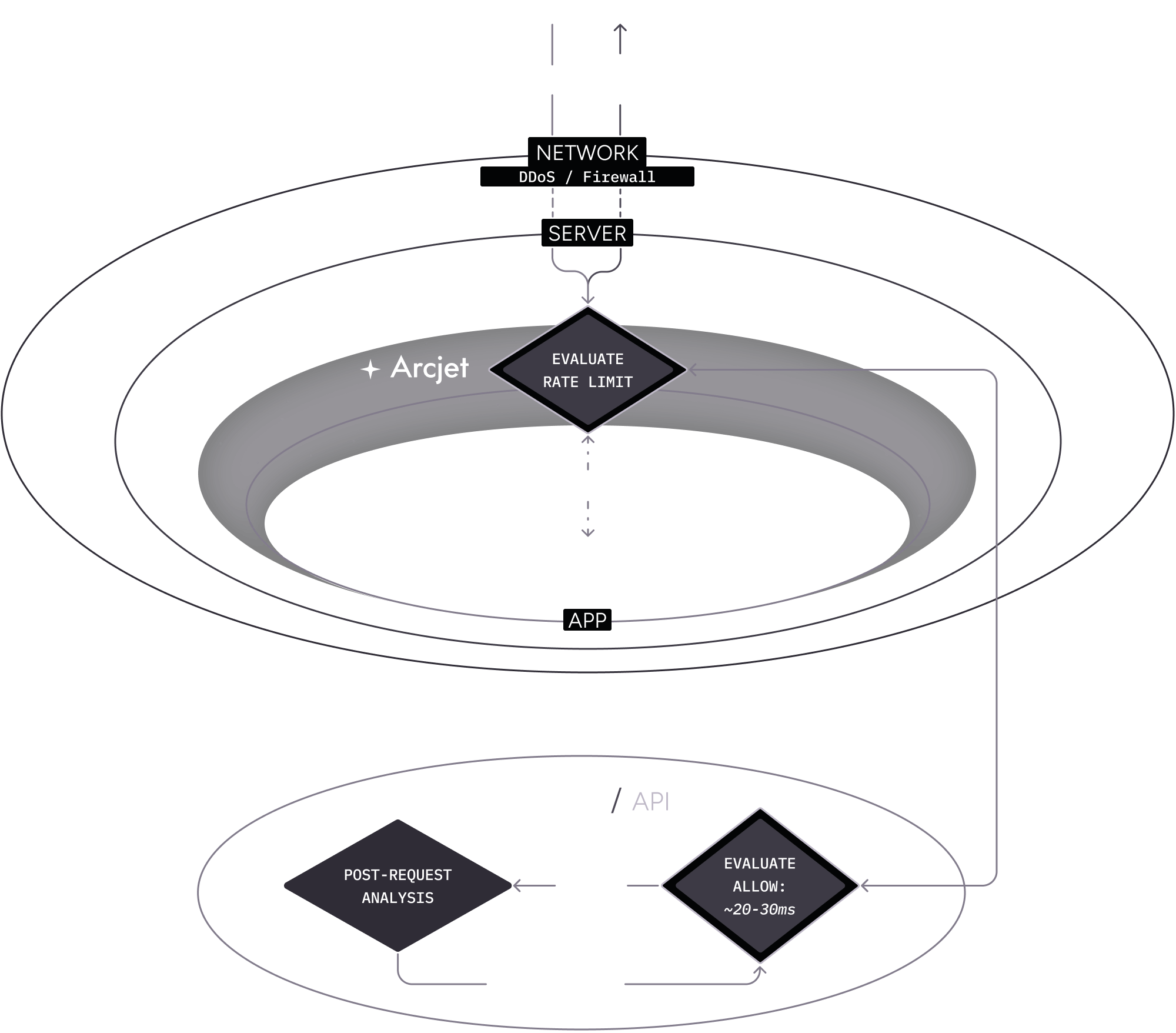
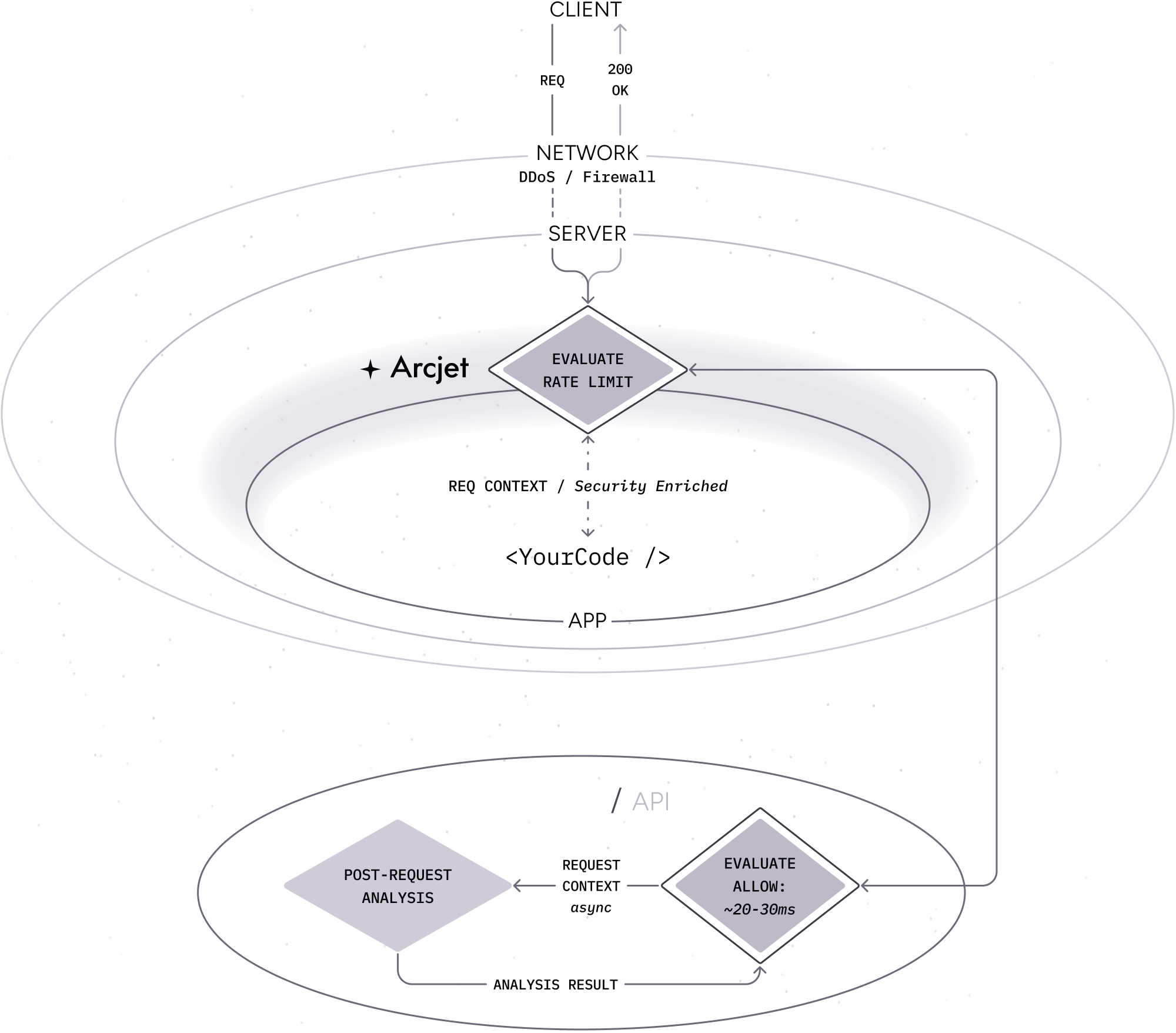
In the example below, the results of the post-request analysis from previous requests are used to inform the decision for the current request.
- A client makes an HTTP request to your application.
- The request is analyzed by the Arcjet SDK based on the rules you configured.
- The SDK returns the result and your application code continues to execute as normal.
- The result is also reported to the Cloud API for post-request analysis. This is used to inform future decisions for that client.
- The client makes another request and the result of the post-request analysis is used to inform the decision. This will be applied if you have configured a Shield rule.
Credits
Section titled “Credits”Arcjet is designed in 🇮🇹 Italy and built in 🇨🇦 Canada and 🇺🇸 USA.